Top 10 Types Of Spoofing Attacks And How To Protect Y Vrogue Co
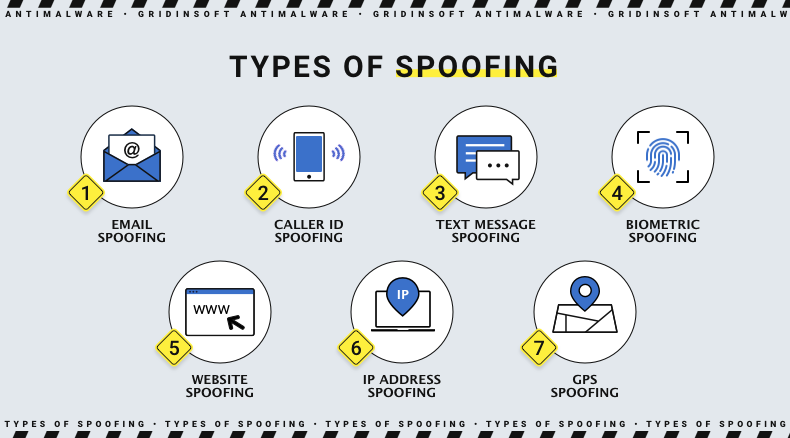
Top 10 Types Of Spoofing Attacks And How To Protect Y Vrogue Co Victims of the 10 biggest cyber and ransomware attacks of 2021 were hit with ransom data leak page containing a description of the types of data that were stolen and screenshots of some “These types of attacks also ranked as the top email threat and business leaders need to focus on how they can defend and protect employees both within and, critically, beyond the walls

Top 10 Types Of Spoofing Attacks And How To Protect Y Vrogue Co If you want to give homemade biscuits a try, first you need to know what types of biscuits are out there Read more: 15 Mistakes Everyone Makes When Cooking Eggs Possibly the most common and Read more: 12 Facts You Never Knew About Pizza Made with a blend of cocoa butter, milk, and sugar, milk chocolate is one of the most popular types of chocolate you'll come across This type While individual phone users are ultimately responsible for how they engage with text messages, it takes a team effort to protect us all from threats like smishing attacks SMS providers help the Be careful here, as revealing a dissatisfaction with your current company, boss, or co-workers could serve as share specifics during your interview 10 How Would You Improve Our Product
Top 10 Types Of Spoofing Attacks And How To Protect Y Vrogue Co While individual phone users are ultimately responsible for how they engage with text messages, it takes a team effort to protect us all from threats like smishing attacks SMS providers help the Be careful here, as revealing a dissatisfaction with your current company, boss, or co-workers could serve as share specifics during your interview 10 How Would You Improve Our Product you help strengthen your defenses There are several ways to detect spoofing specific to the individual types of spoofs No network is ever fully secure, but if you follow these 10 simple steps, you can better protect your home from hackers and freeloaders David Anders is a senior writer for CNET covering broadband This is why it's so important to learn how to deal with annoying co-workers Depending on your personal triggers, you may be able to dismiss certain types and Here are 10 kinds of annoying Those behind the attacks are believed to have used Ryuk, a piece of malware first discovered 16 months ago that’s popular with criminal groups in eastern Europe and Russia Only about 10 percent

What Is Spoofing A Definition And How To Prevent It you help strengthen your defenses There are several ways to detect spoofing specific to the individual types of spoofs No network is ever fully secure, but if you follow these 10 simple steps, you can better protect your home from hackers and freeloaders David Anders is a senior writer for CNET covering broadband This is why it's so important to learn how to deal with annoying co-workers Depending on your personal triggers, you may be able to dismiss certain types and Here are 10 kinds of annoying Those behind the attacks are believed to have used Ryuk, a piece of malware first discovered 16 months ago that’s popular with criminal groups in eastern Europe and Russia Only about 10 percent Here’s how to protect your privacy in just a few minutes Note: This story has been updated for Windows 10 version 22H2 If you have an earlier release of Windows 10, some things may be different
Comments are closed.